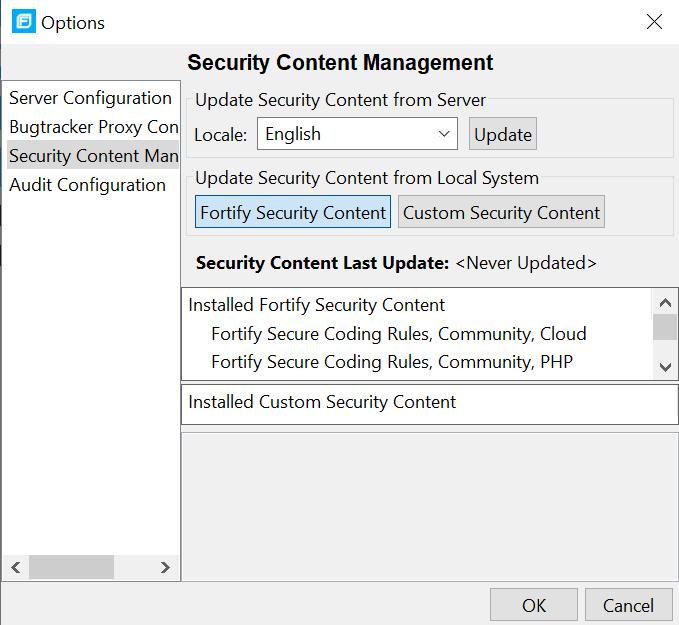
Option 1 (preferred):
- Run the fortifyupdate tool with fortifyupdate -import where is the name of the zip rulepack file.
- Extract the contents of the zip file. You should have a collection of .bin files and an ExternalMetadata folder.
- Copy the .bin files to \Core\config\rules\
- Copy the ExternalMetadata\externalmetadata.xml file to \Core\config\ExternalMetadata\
After completing one of the options above, you can verify the installed content and version via Audit Workbench as shown above, or run fortifyupdate -showInstalledRules on the command-line.
Note that if Fortify is reporting any errors related to externalmetadata.xml, then it is likely not installed in the correct location. There should be no ExternalMetadata file or folder in the \config\rules\ directory. The externalmetadata.xml file should only be in \Core\config\ExternalMetadata\
Method 3: Audit Workbench GUI (via Fortify update server)
Fortify rulepacks can be downloaded and installed via the Audit Workbench via the following steps (note this will likely not work within the VA network, please see Methods 1 or 2):
- Open the Audit Workbench.
- From the Options menu, select “Options…”
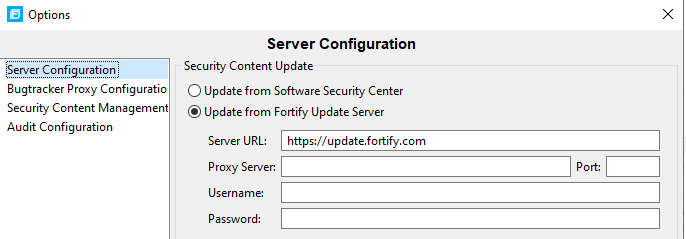
- Under Server Configuration, ensure the servers are configured correctly. If your team is not using Software Security Center, the default settings are typically correct (update from https://update.fortify.com). You can reset to defaults by clicking the “Defaults” button or changing the configuration to match the screenshot below. If your team is using Software Security Center, check the “Update Security Content from Software Security Center” and specify the correct information under the “Software Security Center Configuration” section:
- After setting the correct Server Configuration, click on “Security Content Management” and click the “Update” button as shown in the screenshot below:
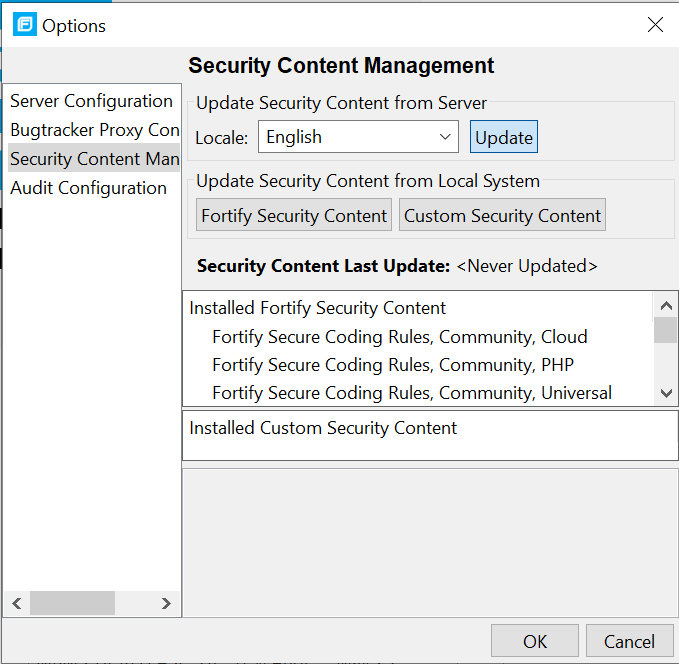
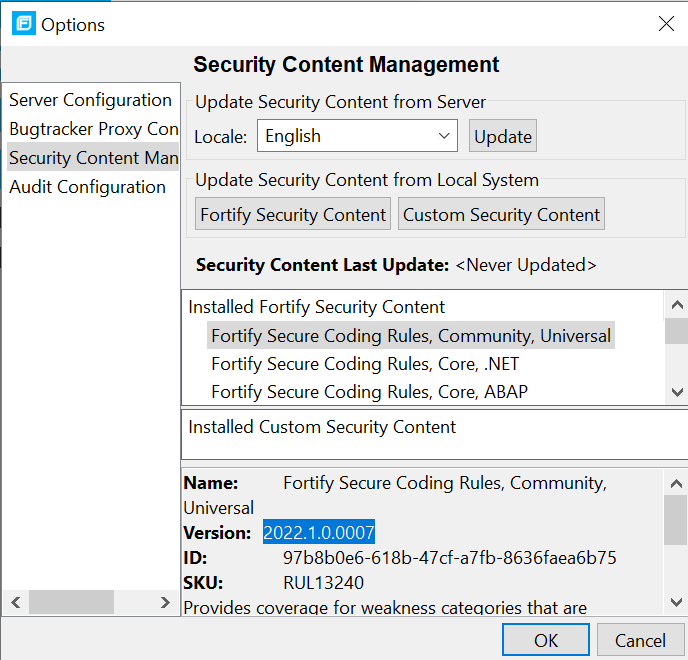
- Once the update process completes, you can check the version installed by selecting one of the items under “Installed Fortify Security Content” and checking the Version field as shown in the screenshot below:
Method 4: Command Line Interface (via Fortify update server)
Alternatively to the Audit Workbench GUI, Fortify rulepacks can also be downloaded and installed via Fortify command line tools as follows (note this will likely not work within the VA network, please see Methods 1 or 2):
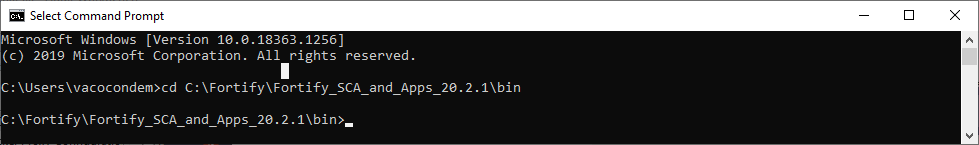
- Open a command prompt and navigate to the Fortify installation “bin” directory, \bin :
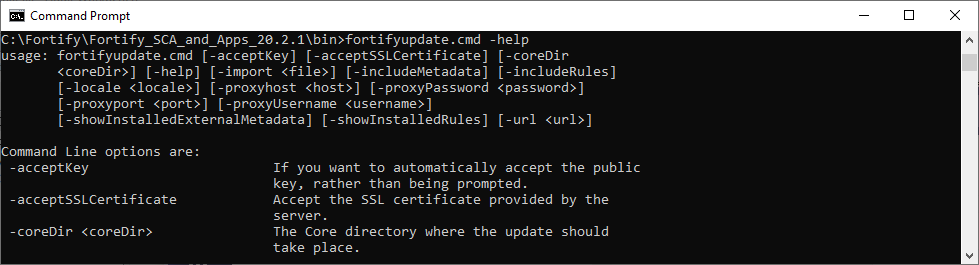
- The fortifyupdate command line tool may be used to facilitate the update. This tool provides several options as shown in the screenshot below:
- If your team is not using Software Security Center, the default settings are typically correct (update from https://update.fortify.com). You can explicitly specify this by running the command as: fortifyupdate -url https://update.fortify.com
- If your team is using Software Security Center, specify the correct information for your server.
- After running the command, you can verify the installed content and version via Audit Workbench as shown above, or run fortifyupdate -showInstalledRules on the command-line.
GitHub at VA (part of VA OIT)
All content is available under Creative Commons Zero v1.0 Universal, except where otherwise stated.